
As of 2024, MySQL ranks as the second most popular database management system globally.
MySQL has become a go-to choice for database management due to its dependable performance, stability, and open-source licensing.
However, its popularity also brings significant security challenges like SQL injection attacks and unauthorized data access.
As cyber threats evolve, protecting MySQL infrastructure is more critical than ever. Advanced tools like ProxySQL are vital for addressing these issues. ProxySQL is a high-performance, open-source SQL proxy tailored for MySQL and other database systems sharing the same protocol. It optimizes database traffic by managing queries more efficiently and enhancing performance and security by supporting configurations that help prevent unauthorized access.
Common MySQL Security Threats

Understanding and mitigating common security threats is essential for maintaining the integrity and availability of your MySQL database. Here are five notable threats to be aware of:
SQL Injection
One of the most prevalent and dangerous threats is SQL injection, which occurs when an attacker manipulates SQL queries by injecting malicious code through application inputs. This can lead to unauthorized data access, manipulation, and, in severe cases, command execution on the database server.
Brute Force Attacks
Attackers use brute force to crack weak database credentials, gaining unauthorized access. Such attacks often exploit simple or default passwords, underscoring the importance of strong, complex passwords and account lockout policies.
Denial of Service (DoS)
By overwhelming the database with excessive requests, attackers can render the database services unavailable to legitimate users, disrupting operations and potentially leading to data loss.
Data Leaks
Improperly configured databases or weak access controls can lead to data leaks, exposing sensitive information publicly or to unauthorized parties. This compromises data confidentiality and can have legal and reputational repercussions.
Malware and Ransomware
These malicious software programs can be installed on database servers through vulnerabilities, leading to data theft, database encryption, or total loss of database control. Ensuring your database and its operating environment are regularly updated and monitored is crucial to preventing malware infections.
Best Practices to Protect Your MySQL Infrastructure
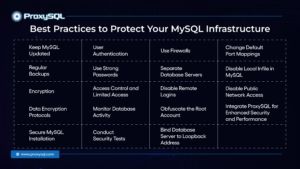
1. Keep MySQL Updated
Failing to update your MySQL server exposes your infrastructure to known vulnerabilities and security breaches, which could lead to significant operational disruptions and data compromises. It is imperative to consistently upgrade to the latest MySQL version, as this process introduces essential security patches and performance enhancements. By staying updated, you proactively shield your database from evolving cyber threats, maintaining a strong defense and ensuring operational integrity.
2. Regular Backups
Neglecting to perform backups can lead to irreversible data loss, severely impacting your business operations and data integrity. A consistent backup protocol is imperative to maintain your MySQL database’s resilience against data corruption, system failures, or other unforeseen events. Implement scheduled and manual backups to secure copies of your database at regular intervals, ensuring that you can restore your system to a functional state swiftly and efficiently in any contingency.
3. Encryption
Unencrypted data is susceptible to unauthorized access and potential breaches, posing a severe risk to the confidentiality and integrity of sensitive information stored within your MySQL database. Employ encryption techniques to secure data at rest, effectively transforming sensitive data into unreadable formats that can only be deciphered with specific decryption keys. Implementing data encryption is a critical component of a comprehensive data protection strategy that ensures compliance with data protection regulations, shields against data breaches, and maintains trust by safeguarding information.
4. Data Encryption Protocols
Beyond securing data at rest, it is equally important to protect data in transit to prevent interception and tampering as it moves across networks. Implement strong encryption protocols, such as TLS (Transport Layer Security), to create a secure channel for data exchange. This prevents potential attackers from capturing or altering sensitive information during transmission. Regularly update and configure your encryption settings to use only strong ciphers and to disable outdated protocols, ensuring that data communications meet current security standards and safeguard against the latest threats.
5. Secure MySQL Installation
A standard MySQL installation comes with default settings that may not suit the specific security needs of your environment and could leave your database vulnerable to attacks. Customizing these settings during the initial setup is crucial to enhance security. Begin by altering default configurations such as passwords, user permissions, and network accessibility to minimize potential attack vectors. Additionally, disable any unused database features or services to reduce exposure further. By taking these steps at installation, you effectively fortify your database against unauthorized access and establish a strong foundation for ongoing database security management.
6. User Authentication
Weak authentication practices can expose your MySQL database to unauthorized access, leading to data breaches and potential compliance violations. To mitigate these risks, implement stringent authentication mechanisms. This involves configuring MySQL to use strong, multifactor authentication that requires more than one form of verification, dramatically reducing the likelihood of unauthorized access.
Consider integrating authentication protocols that combine something the user knows (a password), something the user has (a security token), and something the user is (biometric verification). Additionally, routinely audit and update authentication methods to close gaps as new security threats emerge. This diligent focus on authentication secures your database and reinforces your organization’s overall security posture.
7. Use Strong Passwords
Simple or default passwords can easily be compromised, leaving your MySQL database vulnerable to brute-force attacks. Enforcing a complex password policy is essential for safeguarding access to your database. Require passwords that include a mix of upper- and lowercase letters, numbers, and special characters. Additionally, a minimum password length must be set, and regular password expiration must be implemented to compel users to change their credentials periodically.
Educate users on the importance of using unique passwords for different systems and encourage the use of password managers to maintain the security of their credentials. This policy not only strengthens individual user security but also enhances the overall protection of your database infrastructure.
8. Access Control and Limited Access
Effective access control and adherence to the principle of least privilege are critical for securing your MySQL database. Establish role-based access controls (RBAC) to define and limit user permissions strictly to the necessities of their job functions. This minimizes the risk of unauthorized access and data breaches by ensuring that users can access only the data essential for their roles.
Neglecting these measures can lead to overprivileged accounts, and prime exploitation targets. This could lead to significant security incidents, compliance violations, and reputational harm. To maintain a secure and compliant database environment, regularly review and adjust permissions in line with changes in user roles and responsibilities.
9. Monitor Database Activity
Continuous database activity monitoring is imperative to identify and address unauthorized or anomalous transactions that could indicate a security breach. Implement comprehensive logging of all database actions, including data access, alterations, and failed login attempts. Utilize advanced monitoring tools that employ real-time analytics to alert administrators to unusual activity patterns, such as unexpected access times, high data retrieval volumes, or changes from unrecognized IP addresses.
The absence of diligent monitoring can lead to delayed detection of security incidents, allowing malicious actors to exploit data unnoticed. This can cause extensive damage to data integrity and organizational reputation. Regular audits of log files and prompt investigation of alerts are crucial in maintaining your database’s security and operational integrity.
10. Conduct Security Tests
Routine security assessments are crucial for maintaining the integrity of your MySQL database. Establish a program that includes penetration testing, vulnerability scans, and security audits to detect flaws in your database security proactively. These evaluations should mimic potential attack vectors to uncover configuration, software version, or access control weaknesses.
Failure to conduct these tests can lead to undetected vulnerabilities, exposing your database to potential breaches. Regularly identifying and addressing security issues protects your data and ensures compliance with regulatory standards.
11. Use Firewalls
Deploying firewalls is a fundamental security measure to protect your MySQL database from unauthorized access. Firewalls are a barrier between your database and potential threats, filtering incoming and outgoing network traffic based on predetermined security rules. Configure your firewalls to block unauthorized IP addresses, restrict access to certain ports, and effectively manage traffic to and from the database.
Without adequate firewall protection, your database remains vulnerable to attacks such as SQL injections and unauthorized access attempts. Properly implemented firewalls help prevent these threats by ensuring that only legitimate and necessary communications reach your database, enhancing its overall security posture.
12. Separate Database Servers
Isolating your MySQL database servers from other network segments is a critical strategy for minimizing the risk of cross-system breaches. By deploying database servers on dedicated hardware or within isolated virtual environments, you effectively shield sensitive data from attacks that might compromise less secure areas of your network. This separation limits the scope of potential security incidents and simplifies security management by confining database traffic to controlled pathways.
Failure to segregate database servers can lead to widespread system vulnerabilities, where an attack on one part of the network can easily extend to the database. Implementing strict network segmentation ensures that your database’s integrity remains intact even if other segments are compromised, safeguarding against cascading security failures.
13. Disable Remote Logins
Limiting remote logins to your MySQL database is a critical security measure to reduce potential access points for attackers. Disable remote login capabilities by default and enable them only when necessary and under stringent controls. When remote access is required, secure it with strong authentication methods and encrypted connections to mitigate the risk of unauthorized access.
Enabling remote logins without appropriate security measures can expose your database to attacks such as brute force or credential theft. By restricting this capability, you effectively minimize the attack surface, reducing the likelihood of external breaches while maintaining controlled access for essential operations.
14. Obfuscate the Root Account
Due to its extensive privileges, the default root account on your MySQL database is a prime target for attackers. To enhance security, it’s essential to obfuscate this account by renaming it and/or disabling its remote access. This practice makes it significantly more challenging for malicious actors to guess which account holds administrative privileges, reducing the risk of targeted attacks.
Leaving the root account with default settings can give attackers a straightforward path to attempt unauthorized access, especially using brute force methods. By altering the root account’s visibility and access, you shield your database from direct threats aimed at exploiting this high-level administrative entry point.
15. Bind Database Server to Loopback Address
Configure your MySQL database server to bind to the loopback address, ensuring it only accepts connections from the host machine. Restricting the server to internal communications significantly reduces the risk of external attacks. This configuration prevents the database from being accessible over the network, which is crucial for protecting sensitive data from remote exploits.
Accessing the server from any network address can expose it to various security threats. Binding to the loopback address effectively blocks these threats, allowing only locally initiated interactions to maintain the security of your database environment.
16. Change Default Port Mappings
Altering your MySQL database’s default port settings is a critical security tactic. Changing from standard port numbers to non-standard ones obscures your database from automated scans targeting commonly used ports. This simple change can significantly reduce the visibility of your database to potential attackers who use scanning tools to find exploitable services.
Using default port numbers makes it easier for attackers to identify and target your database, as these are well-known and frequently checked. Customizing port configurations helps to cloak your database in obscurity, providing an additional hurdle for unauthorized access attempts.
17. Disable Local Infile in MySQL
Leaving local infile enabled may provide an attack vector that could compromise the database and the broader server environment. Disabling MySQL’s local infile feature is an essential security action to prevent unauthorized data imports. This feature allows clients to upload local files to the server during their SQL session, which can be exploited to introduce malicious data or scripts into the database. By turning off the local infile, you close a significant vulnerability, enhancing the security of your database environment.
18. Disable Public Network Access
Configuring your MySQL database to reject connections from public or unknown networks is a critical safeguard. This setting ensures that only trusted, private networks can access the database, significantly reducing the likelihood of exposure to external attacks. By limiting connectivity to known sources, you enhance the security of your data and reduce the potential for unauthorized access.
Permitting public network access can leave your database vulnerable to various attacks, including unauthorized data access and denial of service (DoS) attacks. Ensuring that connections are only possible from secure, controlled networks, which minimizes these risks and helps maintain the integrity and availability of your database services.
19. Integrate ProxySQL for Enhanced Security and Performance
Integrating ProxySQL as a database proxy for your MySQL servers can significantly enhance security and performance. ProxySQL acts as a middleware between your application and your databases, enabling you to implement fine-grained access control, query caching, and query routing without modifying application logic. By using ProxySQL, you can also enforce advanced security policies like blocking queries that do not meet your security standards and limiting user access based on rules that match specific query patterns. Implementing ProxySQL helps mitigate risks by providing an additional layer of abstraction, which can protect your databases from direct exposure to the internet and reduce the risk of SQL injection attacks. Its ability to handle thousands of connections and multiplex them to MySQL servers improves database performance and scalability.
Enhance Your MySQL Security with ProxySQL
As cyber threats become more sophisticated, safeguarding your MySQL database is more crucial than ever. ProxySQL offers a powerful solution that enhances security and performance through intelligent query management.
With ProxySQL, you get:
- Detailed Access Control: Tailor database access with precision, significantly reducing risks like SQL injection.
- Efficient Query Routing: Direct queries to the most appropriate servers, balancing loads and minimizing server stress.
- Scalability: Smoothly handle an increase in connections, allowing your system to expand without sacrificing performance.
Integrating ProxySQL can boost your MySQL setup. Its advanced features secure your data and enhance query response times, ensuring your database system remains efficient under increased demands.
Are you ready to upgrade your database capabilities? Begin the journey to a more secure and efficient database environment today. Contact us today!